It is used for generating primes (/etc/ssh/moduli) for DH key exchange. It is not used in any way for generating SSH keys. How to generate and test the moduli file is explained in separate chapter MODULI GENERATION of manual page for ssh-keygen. For the different key types, what are the recommended minimum -b bit sizes? Nov 30, 2018 The procedure to set up SSH key on Red Hat Enteprise Linux 8 server: On your local desktop type: Install public key into remote RHEL 8 server using: Use ssh for password less login. Nov 02, 2018 On the remote system, edit /.ssh/authorizedkeys and append the output of the cat command above. Now you should be able to connect from your computer to the remote system. No restarts are necessary. For more details, see How to setup SSH passwordless login in Red Hat Enterprise Linux on the Red Hat Customer Portal. I don't like that kind of answer that say 'you shouldn't do that' but don't answer the question. While this may be correct and helpful for the context of the original question, other people may have the same question in a different situation. 'ssh keys should never be generated for another user': That is true in the simple case. Oct 10, 2019 This article showed you how to setup SSH keys so that you don't have to type a password to login to a remote system, to copy files to a remote system, or to copy files between two remote systems. Setting up SSH keys between systems means that you can easily automate tasks such as file manipulation without storing a password in a file. Nov 02, 2018 We often use ssh-copy-id to copy ssh keys from our local Linux computers to RHEL servers in order to connect without typing in a password. This is not only for convenience; it enables you to script and automate tasks that involve remote machines.
I am a new RHEL 8 server sysadmin. How do I configure SSH public key-based authentication for RHEL (Red Hat Enterprise Linux) 8 server?
Introduction – SSH is an acronym for secure shell. It is a suite of cryptographic network protocol. It allows users to log in and transfer files securely over the unsecure network such as the Internet. OpenSSH is an implementation of SSH protocol on RHEL 8. You can log in using RHEL 8 user and password account. However, OpenSSH project recommends log in using a combination of a private and public SSH keys.
Advertisements
Sample set up for our RHEL 8 server
Where,
- You generate a key pair on your Linux/Unix/macOS desktop.
- Place the public key on RHEL 8 server.
- One can unlock public key using a private key stored on your desktop with the help of ssh command.
- When both the public and private key correct you can log in without a password.
How do I set up SSH keys on RHEL 8 server?
The procedure to set up SSH key on Red Hat Enteprise Linux 8 server:
- On your local desktop type:
ssh-keygen - Install public key into remote RHEL 8 server using:
ssh-copy-id user@remote-RHEL8-server-ip - Use ssh for password less login:
ssh user@remote-RHEL8-server-ip
Let us see all commands and steps in details.
How to create the ed25519 or RSA key pair
The syntax is:
ssh-keygen -t ed25519
ssh-keygen -t rsa
ssh-keygen -t rsa -b 4096 -f ~/.ssh/aws-lighsail.key -C 'My AWS SSH Keys'
ssh-keygen -t ed25519 -f ~/.ssh/linode-usa-www1-vps.key -C 'My Linode SSH Keys for www'
Where,
- -t rsa OR -t ed25519 : Specifies the type of key to create. The possible values “dsa”, “ecdsa”, “ed25519”, or “rsa” for SSH protocol version 2.
- -b 4096 : Specifies the number of bits in the key to create.
- -f~/.ssh/aws-lighsail.key : Specifies the filename of the key file.
- -C -C 'My AWS SSH Keys' : Set a new comment.
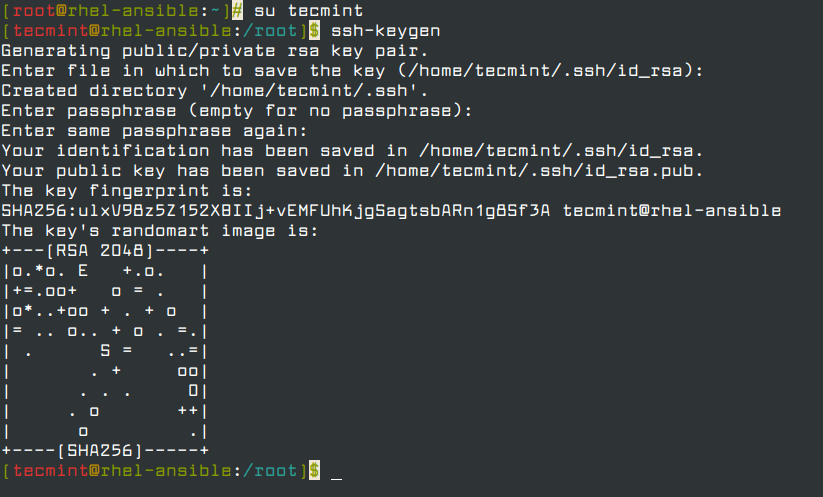
I am going type the following command on my Ubuntu desktop to create the key pair:
$ ssh-keygen -t ed25519
I strongly recommend that you set up a passphrase when prompted.
How to copy the public key

Now our key paid generated and stored in ~/.ssh/ directory. You must copy a public SSH key file named ~/.ssh/id_ed25519.pub (or ~/.ssh/id_rsa.pub if you created RSA key) to the RHEL 8 server. Try the ssh-copy-id command as follows:
$ ssh-copy-id -i ~/.ssh/fileNameHere.pubuser@remote-RHEL8-server-ip
For example:
$ ssh-copy-id -i ~/.ssh/id_ed25519.pub vivek@192.168.2.211
How to log in using ssh and without a password
Now try logging into the machine, with the ssh command as follows:
$ ssh user@rhel-8-server
$ ssh vivek@192.168.2.211
You should be able to log in without a password. If you set up a passphrase, unlock it as follows for your current session so that you don’t have to enter it every time you run ssh, sftp, scp, rsync and other commands:
$ ssh-agent $SHELL
$ ssh-add
Optional settings for root user
Disable root user log in all together on RHEL 8 via ssh. Log in as root user on RHEL 8 and run following to add a user named vivek to wheel group:
# usermod -aG wheel vivek
# id vivek
Allows users in group wheel can use sudo command to run all commands on RHEL 8 server. Ssh generate public key from private linux. Next disable root user login by adding the following line to sshd_config:
# vi /etc/ssh/sshd_config
Disable the password for root login and only allow ssh keys based login:
Save and close the file. Reload the ssh server:
# systemctl reload sshd.service
For more info see “Top 20 OpenSSH Server Best Security Practices“.
Conclusion
You learned how to set up and use SSH keys to manage your RHEL 8 based server. For more info see OpenSSH man pages here.
ADVERTISEMENTS
I recently read that SSH keys provide a secure way of logging into a Linux and Unix-based server. How do I set up SSH keys on a Linux or Unix based systems? In SSH for Linux/Unix, how do I set up public key authentication?
This page explains a public key and shows you how to set up SSH keys on a Linux or Unix-like server. I am assuming that you are using Linux or Unix-like server and client with the following software:
Advertisements
- OpenSSH SSHD server
- OpenSSH ssh client and friends on Linux (Ubuntu, Debian, {Free,Open,Net}BSD, RHEL, CentOS, MacOS/OSX, AIX, HP-UX and co).
What is a public key authentication?
OpenSSH server supports various authentication schema. The two most popular are as follows:
- Passwords based authentication
- Public key based authentication. It is an alternative security method to using passwords. This method is recommended on a VPS, cloud, dedicated or even home based server.
How to set up SSH keys
Steps to setup secure ssh keys:
- Create the ssh key pair using ssh-keygen command.
- Copy and install the public ssh key using ssh-copy-id command on a Linux or Unix server.
- Add yourself to sudo or wheel group admin account.
- Disable the password login for root account.
- Test your password less ssh keys login using ssh user@server-name command.
Let us see all steps in details.
How do I set up public key authentication?
You must generate both a public and a private key pair. For example:
Where,
- server1.cyberciti.biz – You store your public key on the remote hosts and you have an accounts on this Linux/Unix based server.
- client1.cyberciti.biz – Your private key stays on the desktop/laptop/ computer (or local server) you use to connect to server1.cyberciti.biz server. Do not share or give your private file to anyone.
Redhat Generate Exchange Ssh Keys To Mac
In public key based method you can log into remote hosts and server, and transfer files to them, without using your account passwords. Feel free to replace server1.cyberciti.biz and client1.cyberciti.biz names with your actual setup. Enough talk, let’s set up public key authentication. Open the Terminal and type following commands if .ssh directory does not exists:
1: Create the key pair
On the computer (such as client1.cyberciti.biz), generate a key pair for the protocol.
Sample outputs:
You need to set the Key Pair location and name. I recommend you use the default location if you do not yet have another key there, for example: $HOME/.ssh/id_rsa. You will be prompted to supply a passphrase (password) for your private key. I suggest that you setup a passphrase when prompted. You should see two new files in $HOME/.ssh/ directory:
- $HOME/.ssh/id_rsa– contains your private key.
- $HOME/.ssh/id_rsa.pub – contain your public key.
Optional syntax for advance users
The following syntax specifies the 4096 of bits in the RSA key to creation (default 2048):
$ ssh-keygen -t rsa -b 4096 -f ~/.ssh/vps-cloud.web-server.key -C 'My web-server key'
Where,
- -t rsa : Specifies the type of key to create. The possible values are “rsa1” for protocol version 1 and “dsa”, “ecdsa”, “ed25519”, or “rsa” for protocol version 2.
- -b 4096 : Specifies the number of bits in the key to create
- -f ~/.ssh/vps-cloud.web-server.key : Specifies the filename of the key file.
- -C 'My web-server key' : Set a new comment.
2: Install the public key in remote server
Use scp or ssh-copy-id command to copy your public key file (e.g., $HOME/.ssh/id_rsa.pub) to your account on the remote server/host (e.g., nixcraft@server1.cyberciti.biz). To do so, enter the following command on your client1.cyberciti.biz:
OR just copy the public key in remote server as authorized_keys in ~/.ssh/ directory:
A note about appending the public key in remote server
On some system ssh-copy-id command may not be installed, so use the following commands (when prompted provide the password for remote user account called vivek) to install and append the public key:
3: Test it (type command on client1.cyberciti.biz)
The syntax is as follows for the ssh command:
Or copy a text file called foo.txt:
You will be prompted for a passphrase. To get rid of passphrase whenever you log in the remote host, try ssh-agent and ssh-add commands.
Enable Ssh Rhel 7
What are ssh-agent and ssh-add, and how do I use them?
To get rid of a passphrase for the current session, add a passphrase to ssh-agent and you will not be prompted for it when using ssh or scp/sftp/rsync to connect to hosts with your public key. The syntax is as follows:
Type the ssh-add command to prompt the user for a private key passphrase and adds it to the list maintained by ssh-agent command:
Enter your private key passphrase. Now try again to log into user@server1.cyberciti.biz and you will not be prompted for a password:
One can list public key parameters of all identities with the -L option:
ssh-add -L
Deleting all private keys from the ssh-agent can be done with the -D option as follows:
ssh-add -D
When you log out kill the ssh agent, run:
kill $SSH_AGENT_PID
You can also add something like the below to your shell startup to kill ssh-agent at logout:
trap 'kill $SSH_AGENT_PID' 0
4: Disable the password based login on a server
Login to your server, type:
Edit /etc/ssh/sshd_config on server1.cyberciti.biz using a text editor such as nano or vim:
Openssh Redhat
Warning: Make sure you add yourself to sudoers files. Otherwise you will not able to login as root later on. See “How To Add, Delete, and Grant Sudo Privileges to Users on a FreeBSD Server” for more info.
$ sudo vim /etc/ssh/sshd_config
OR directly jump to PermitRootLogin line using a vim text editor:
$ sudo vim +/PermitRootLogin /etc/ssh/sshd_config
Find PermitRootLogin and set it as follows:
Save and close the file. I am going to add a user named vivek to sudoers on Ubuntu Linux:
# adduser vivek
Finally, reload/restart the sshd server, type command as per your Linux/Unix version:
5: How to add or replace a passphrase for an existing private key?
To to change your passphrase type the following command:
ssh-keygen -p
6: How do I backup an existing private/public key?
Just copy files to your backup server or external USB pen/hard drive:
How do I protect my ssh keys?
- Always use a strong passphrase.
- Do not share your private keys anywhere online or store in insecure cloud storage.
- Restrict privileges of the account.
How do I create and setup an OpenSSH config file to create shortcuts for servers I frequently access?
See how to create and use an OpenSSH ssh_config file for more info.
Red Hat Generate Exchange Ssh Keys Code
Conclusion
This page explained how to set up ssh keys for authentication purposes. For more info see the following resources:
- Man pages – ssh-keygen(1)
- OpenSSH project homepage here.
Red Hat Generate Exchange Ssh Keys Download
And, there you have it, ssh set up with public key based authentication for Linux or Unix-like systems.
Redhat Generate Exchange Ssh Keys To Computer
ADVERTISEMENTS

